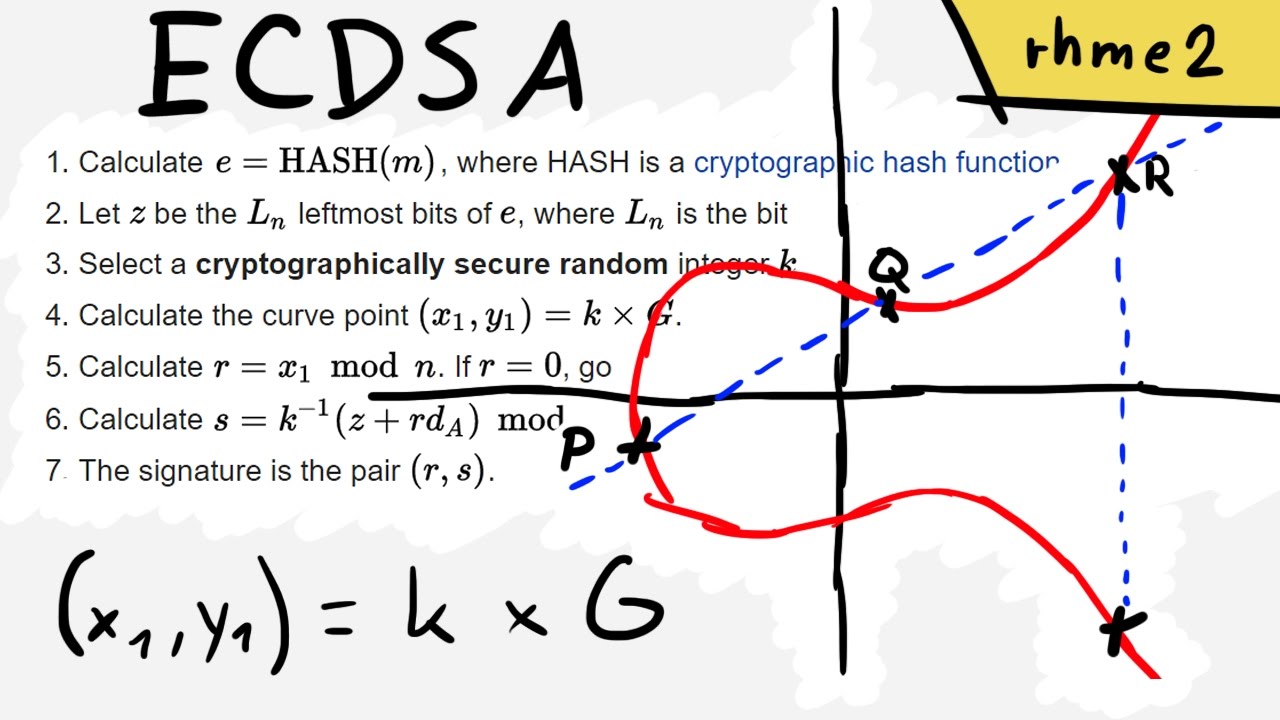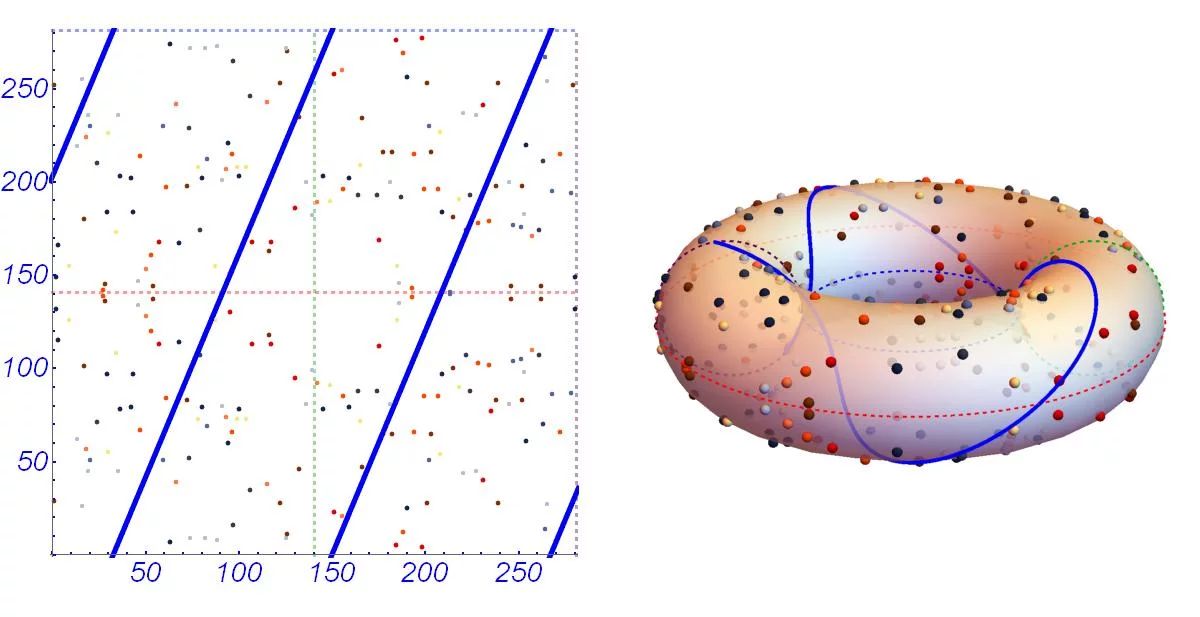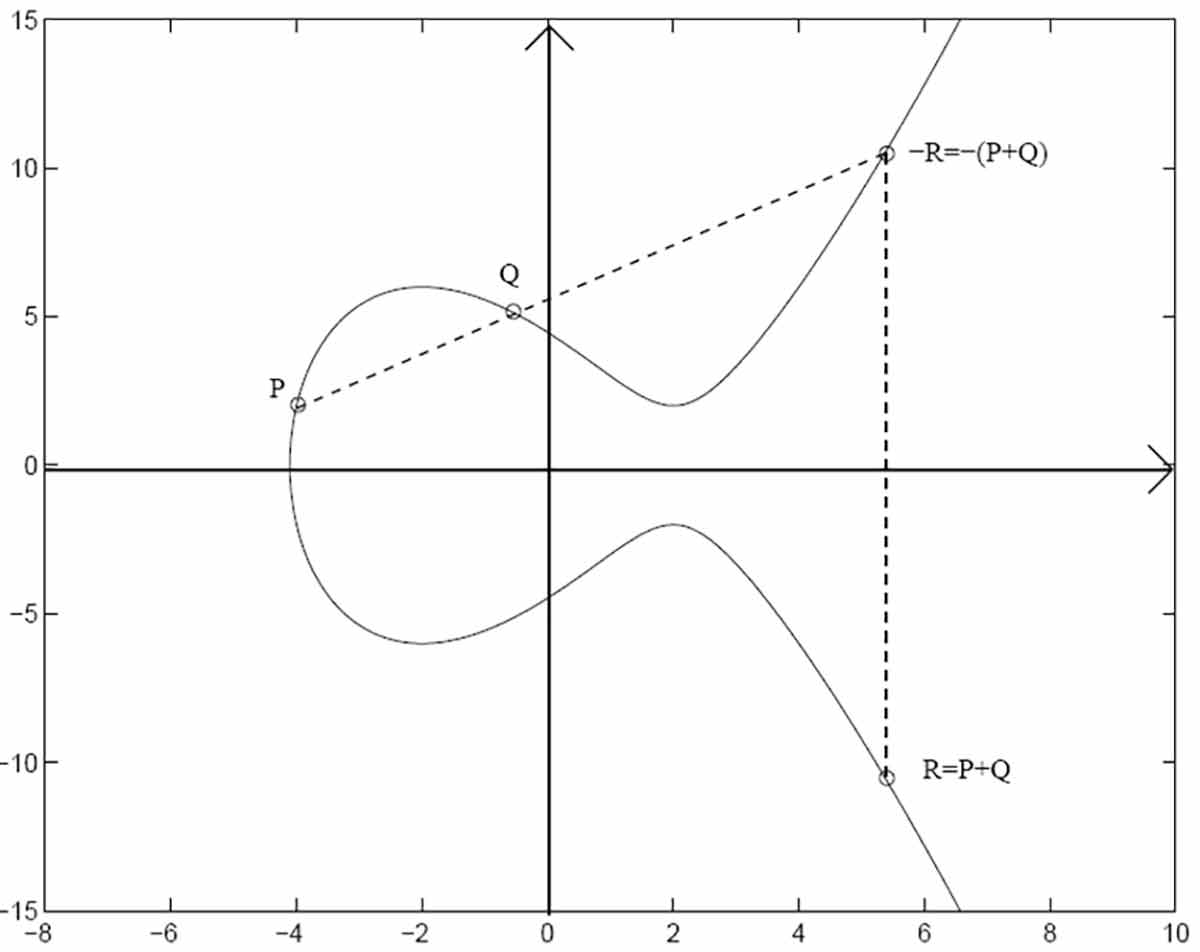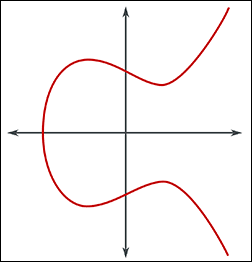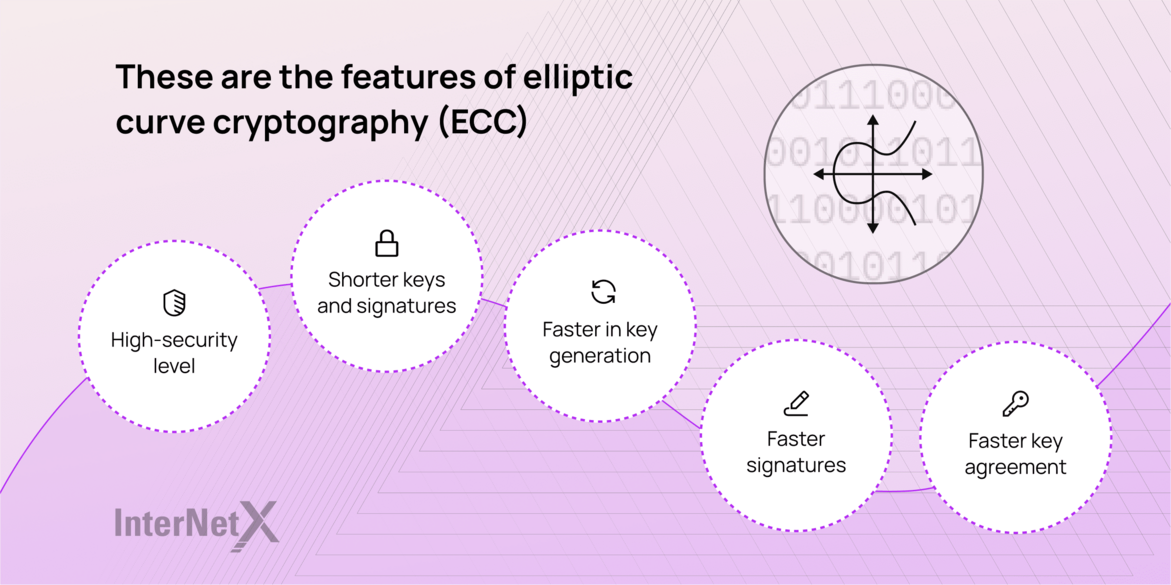
A generalized framework for elliptic curves based PRNG and its utilization in image encryption | Scientific Reports

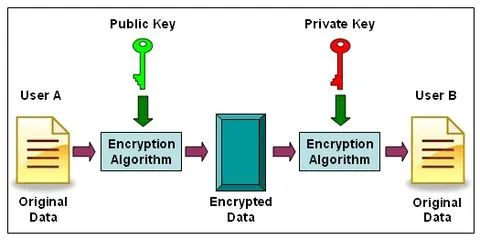
Integration of Quantum Cryptography and Elliptic Curve Cryptography for... | Download Scientific Diagram
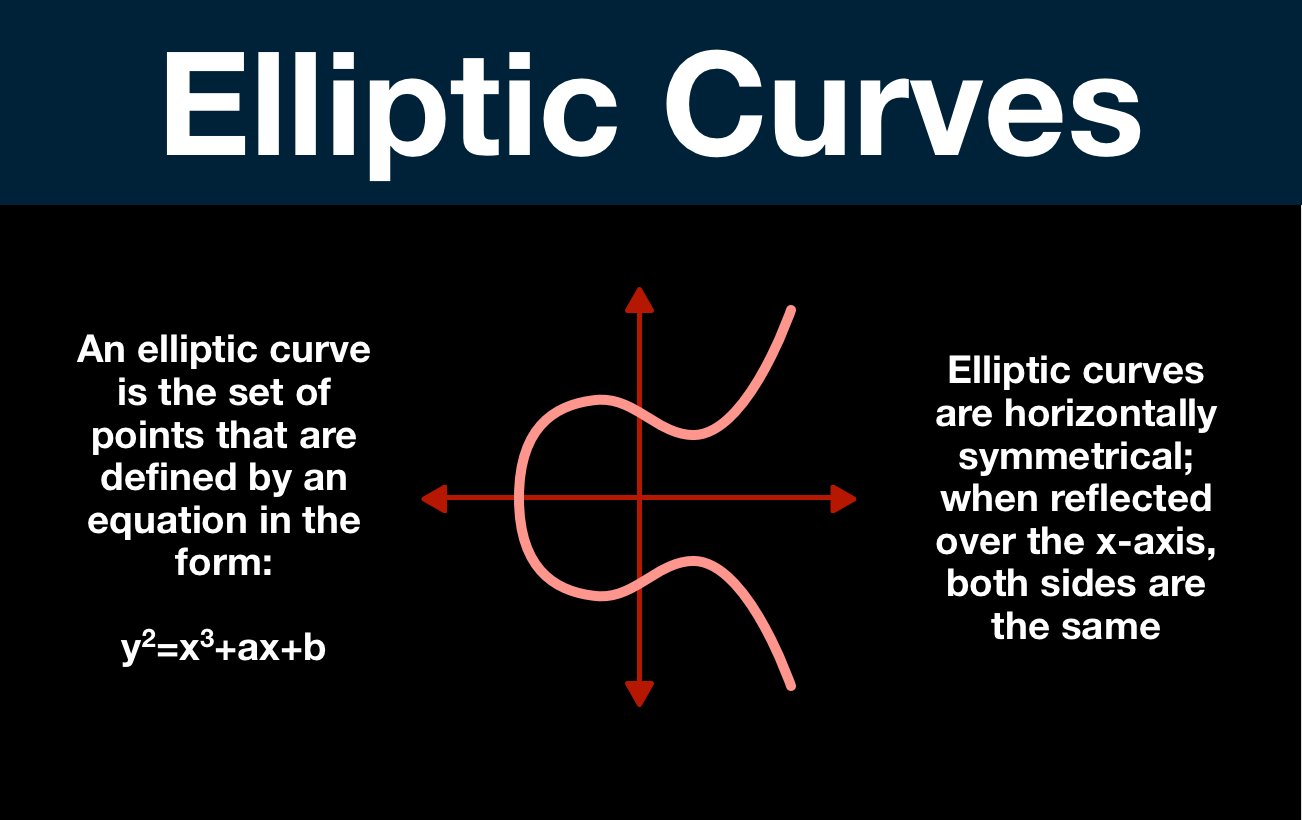
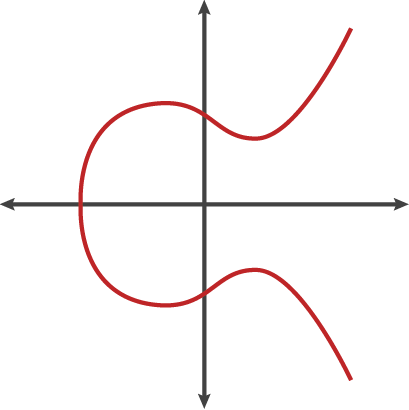
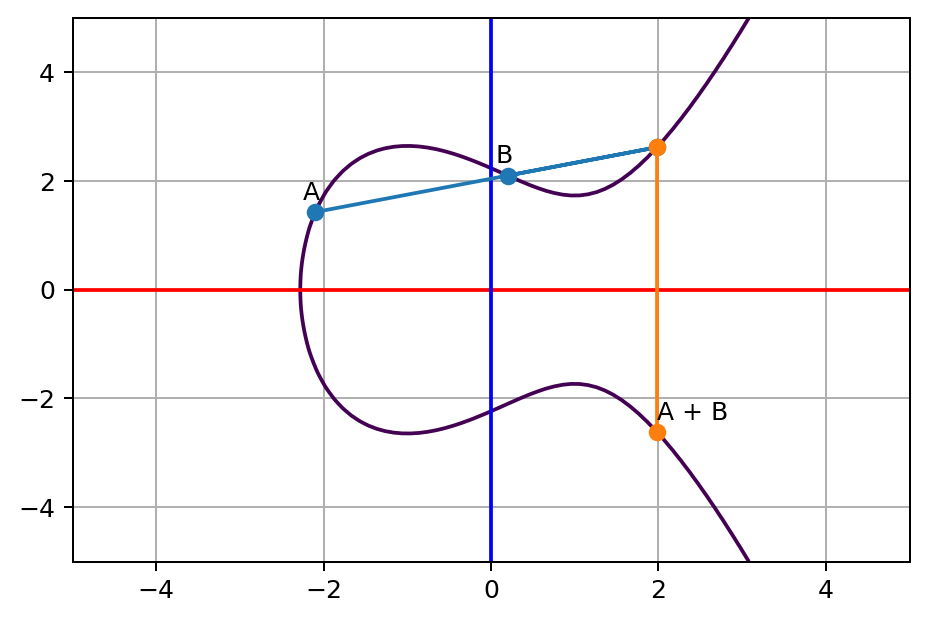
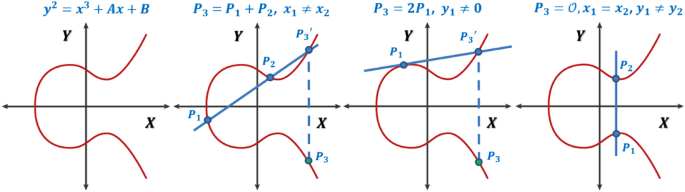
Tyrannosaurus Haym on Twitter: "(1/25) Cryptography Fundamentals: Elliptic Curve Cryptography Elliptic Curve Cryptography is (one of) our strongest cryptographic tools, vastly more secure than its predecessors. But... how does the moon math

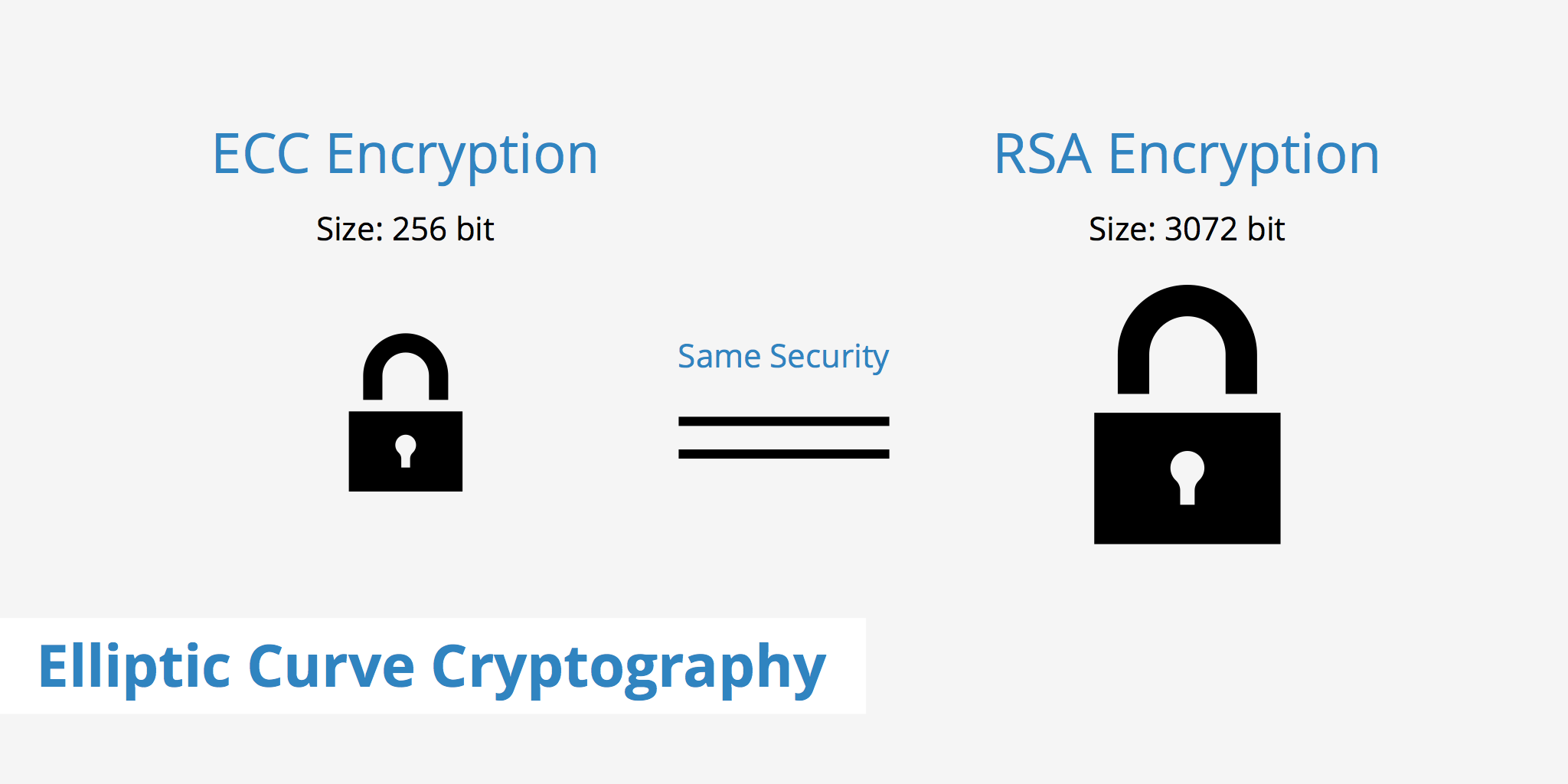
Enhancing Data Encryption using Elliptic Curve Cryptography (ECC) Algorithm in 4G Networks | Semantic Scholar
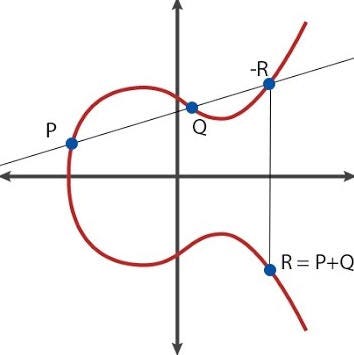
Part 2 — Is Elliptic Curve Cryptography (ECC) a step towards something more — Understanding ECC | by Peter Reid | Medium